It's external. http://cve.mitre.org/
This list is the begging of all. Each line has this format:
CVE-<number> (<short description>)<status>: <description>The repo can be found at svn+ssh:svn.debian.org/svn/secure-testing
We get notified via either email
(http://lists.alioth.debian.org/mailman/listinfo/secure-testing-commits)
of every SVN commit, by RSS feed
(http://svn.debian.org/wsvn/secure-testing/?op=rss&rev=0&sc=0&isdir=1)
or via the CIA bot on #debian-security on OFTC. For example, the bot
will say in the channel:
.
17:14 < CIA-1> joeyh * r2314 /data/CVE/list: automatic update
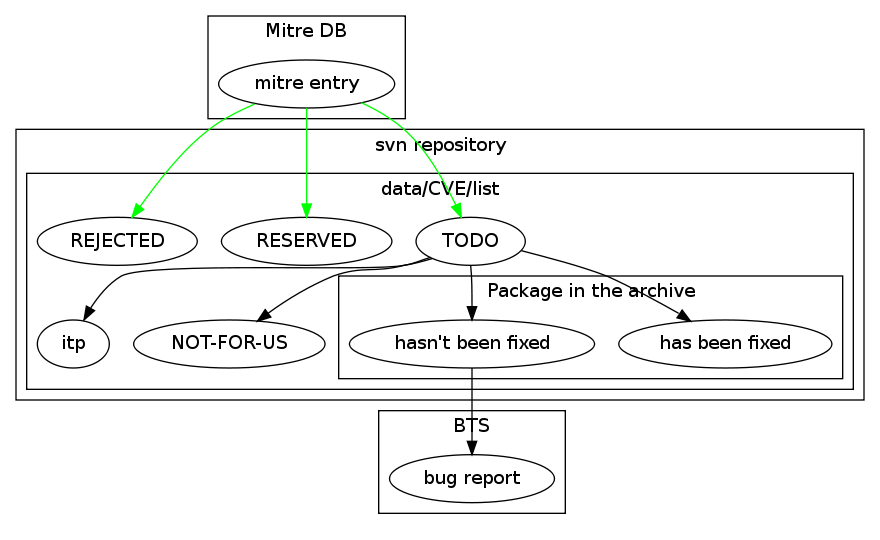
Twice a day a cronjob runs that pulls down the latest full CVE lists from Mitre, this automatically gets checked into data/CVE/list. The Mitre update typically manifests in new CVE entries. So what we do is to update our svn repository and then edit data/CVE/list and look for new TODO entries. These will often be in blocks of 10-50 or so, depending on how many new issues they have assigned.
Several security problems have coordinated dates of public disclosure, i.e. a CVE identifier has been assigned to a problem, but it's not public yet. Also, several vendors have a pool of CVE ids they can assign to problems that are detected in their products. Such entries are marked as RESERVED in the tracker:
CVE-2005-1432RESERVEDSometimes there are CVE assignments that later turn out to be duplicates, mistakes or non-issues. These items are reverted and turned into REJECTED entries:
CVE-2005-4129REJECTEDIf it is a package that someone has filed an RFP or ITP for, then that is also noted, so it can be tracked to make sure that the issue is resolved before the package enters the archive: .
CVE-2004-2525 (Cross-site scripting (XSS) vulnerability in compat.php in Serendipity ...)- serendipity <itp> (bug #312413)If it is a package in Debian, look to see if the package is affected or not (sometimes newer versions that have the fixes have already been uploaded).
If the version has been fixed already, note the package name and the Debian version that fixes it and assign a severity level to it, for example: .
CVE-2005-2596 (User.php in Gallery, as used in Postnuke, allows users with any Admin ...)- gallery 1.5-2 (medium)If it hasn't been fixed, we determine if there has been a bug filed about the issue, and if not, file one and then note it in the list (again with a severity level): .
CVE-2005-3054 (fopen_wrappers.c in PHP 4.4.0, and possibly other versions, does not ...)- php4 <unfixed> (bug #353585; medium)- php5 <unfixed> (bug #353585; medium)Twice a day a cronjob runs that pulls down the latest full CVE lists from Mitre, this automatically gets checked into data/CVE/list. See: #mitre entry -> TODO, #mitre entry -> RESERVED, #mitre entry -> REJECTED This script also syncs that file with other lists like data/DSA/list and data/DTSA/list.